Learn about three different types of security solutions that can help your company prepare for the future.
When you hear the word insecure are you more likely to think of personal anxieties and fears, or unlocked doors, phishing emails, and spies dangling from the ceiling in an attempt to access and steal your data, Tom Cruise style? Either way, when you think of your business’ security, do you feel insecure?
Luckily, we are here to highlight 3 specific types of security that can help your business shake off all those insecurities and become a bolder, more secure version of its best self! Before learning how each of these systems can help protect your business, first, we need to go back in time and understand how each of them came about.
CYBERSECURITY
The Worm
In 1970, a man named Robert Morris created the first malicious computer worm, a piece of software that looks for other computers on the network and infects them. This worm came after the creation of the first computer worm – called the Creeper – which was created to help the earliest incarnations of software engineers determine if a program was capable of leaving a trail when moving throughout a network.
Unlike the Creeper, Morris’s worm was not used for research. In the end, it infected so many computers that it crashed the early internet (ARPANET), causing it to become slow and sluggish. Morris “said” he only created the worm because he was “curious” to see if he could find out how big the ARPANET was. So unless the ingenuity of the worm was a fluke for Morris, it’s safe to assume there was likely malicious intent behind it. Thankfully, the precursor to the internet was so comparatively small next to the leviathan of today’s internet that it was easy for officials to track the worm back to him and he ended up getting fined and put on probation.
What Now?
Fast forward to 2021 – cyber threats have increased by 600% and are almost impossible to track down and address. If one person could do all that damage in the 1970s, imagine how much damage could be done decades later, with even better technology, attacking an almost infinite amount of data? Let’s just say you wouldn’t want to find out.
So what can your company do? Well, according to a survey from the Ponemon Institute,
60% of breaches in 2019 involved unpatched vulnerabilities within systems.
That means that the best thing you and your company can do is to try to prevent these types of attacks – build a drawbridge, dig a moat, put up a wall – better yet, call Summit Technology and we’ll help you through it ;). But seriously, as a Managed Service Provider, we have the ability and skills to help you configure your firewalls, encrypt your data, and implement Data Loss Prevention (DLP) policies and retention policies so you can keep your data safe.
60% of breaches in 2019 involved unpatched vulnerabilities within systems.
No matter what, do something today. It is easier to prevent a mess than to clean up a mess.
Pros
Cons
ACCESS CONTROL
The Door Lock
Access control has been around for thousands of years – 6,000 to be exact – ever since the first teenagers decided they knew more than their parents and just needed some privacy. No, but seriously, the first access control systems were just simple door locks. Of course door locks have evolved a little in the last 6,000 years, but the pins-and-bolts design is basically the same. Robert Barron invented the first metal door lock that required a key to release the bolt in 1778, leading to major changes to the lock and key industry. Like many industrious miscreants before them, lock-picks and thieves got to work, and within 200 years the standard door lock needed an upgrade.
Cloud Solution
It wasn’t until 200 years later, in the 1980s, that the world upgraded their door locks to an electrified magstripe card system. Think of hotel key cards – it works while you’re staying in the room but can be turned off when you leave. Even though this new system was a bit safer and more convenient, there was still an issue with the magstripe demagnetizing – causing the card to become useless. Not to mention hackers could still try to manipulate the system and gain access. There needs to be a better way…
By the early 2000s, Radio Frequency Identification (RFID) systems were on their way to revolutionizing the world of access control. RFID uses electromagnetic fields to identify and track a card or fob in seconds! Once the system controller recognizes the card, it will only open if that specific card is authorized to access a specific door or area.

In time we replaced clunky on-premise access control systems with cloud-based controllers, creating an entirely new way to improve access security. Now that we could manage and store the access credentials and history in the cloud, companies began creating tools to combine standard RFID cards or chips with cloud-based control systems and new hardware that can be configured to allow Bluetooth, Near-field communications (NFC) devices, or access through a mobile device.
Don’t get stuck in the past – update that door lock today!
Pros
Cons
VIDEO SURVEILLANCE
Lights! Camera! Rockets?
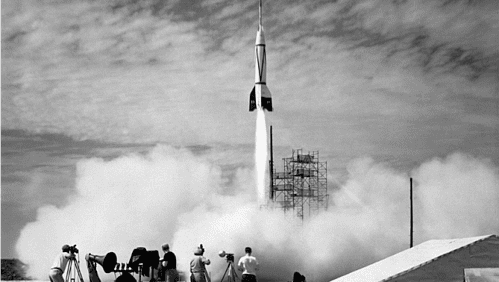
Video camera systems have been around since the 1920s but were only really used in the entertainment industry for live broadcasts. It wasn’t until the development of closed-circuit systems (CCTV) – a type of video surveillance that sends a signal to a specific place or monitor – that people started using video camera systems as video surveillance systems.
The first CCTV video surveillance system was installed in Germany in 1942 and was used by the German military to safely observe the launch of V2 rockets from a distance. Who knew? When the U.S got a hold of those systems, they were quickly adapted for government and commercial security. These systems were perfect for helping protect businesses and organizations keep an extra eye on things. The only issue with early video surveillance was the inability to record the live footage. There had to be someone who constantly monitored the cameras. What a huge waste of time! But don’t worry, it gets better.
 Better Technology
Better Technology
In came the videocassette recorder (VCR)! This solution was introduced in the 1970s and could actually record video AND playback the recording. Now we’re getting somewhere. Next came the Internet Protocol (IP) camera – a type of camera that only requires a local network rather than a recording device to send data. These cameras were more complex and a little harder to sell, but as more and more companies started to understand how this type of technology worked, IP cameras gained more and more popularity. But was this the best they could do?
Definitely not! Eventually, cloud-based video surveillance systems were introduced! This solution uses a type of IP camera that doesn’t require on-site hardware or complex configurations and is connected to the cloud. That means that you get more data storage, automatic updates, and convenient access to your footage through a secure application. Now that is what we like to hear!
9 out of 10 businesses are currently using cloud technology, don’t be the one who isn’t.
Pros
Cons
The most important concept to take away from this article is to find a security solution. Talk to us about how we can find you a solution that is Simple. Convenient. Secure.
If you still have questions about any of these types of security systems, you can contact us at learnmore@greatservice.com or fill out our contact us form.
Subscribe to stay up on all the ways you can improve your company’s IT.



